What is a SBOM?
One of my friends messaged me on LinkedIn today and asked “What is this SBOM you keep talking about?” I realized that he’s right and I should probably explain what an SBOM is. So, let me start by defining the acronym: SBOM refers to a “Software Bill of Materials”.
An SBOM is a complete inventory of all the software and dependencies of an application and is typically delivered in the form of a JSON or XML document. Although, for some vendors, the “SBOM” is really just their web portal and not a deliverable file. This matters as many customers are looking to provide SBOMs for compliance requirements made by partners or customers. In most cases, the requestor is looking for a file to be delivered, and at some point, inspected for accuracy.
Why is an SBOM critical? Well, one reason is that they provide visibility into what is actually *inside* an application, but it also helps identify the software supply chain underpinning a particular application.
Wikipedia defines an SBOM this way:
“A software bill of materials (SBOM) is a list of components in a piece of software. Software vendors often create products by assembling open source and commercial software components. The SBOM describes the components in a product. It is analogous to a list of ingredients on food packaging: where you might consult a label to avoid foods that may cause allergies, SBOMs can help organizations or persons avoid consumption of software that could harm them.”
Why is everybody talking about SBOM now?
The need for something like an SBOM specification has existed for a while now but has become more necessary in the last two years driven by several high-profile security incidents. In particular, the SolarWinds incident in early 2020 as well as ongoing issues with NPM have made it obvious that there needed to be more governance around the software supply chain than there was.
Applications have become increasingly complex which in turn makes securing and managing those applications more difficult. Cloud-native services and open source make up a growing part of the average modern web application. Software engineering teams don’t necessarily understand how adopting these new technologies or services changes the threat model for their applications. The SBOM is meant, in part, to at least make these components visible to the naked eye so teams can understand the scope and breadth of their applications.
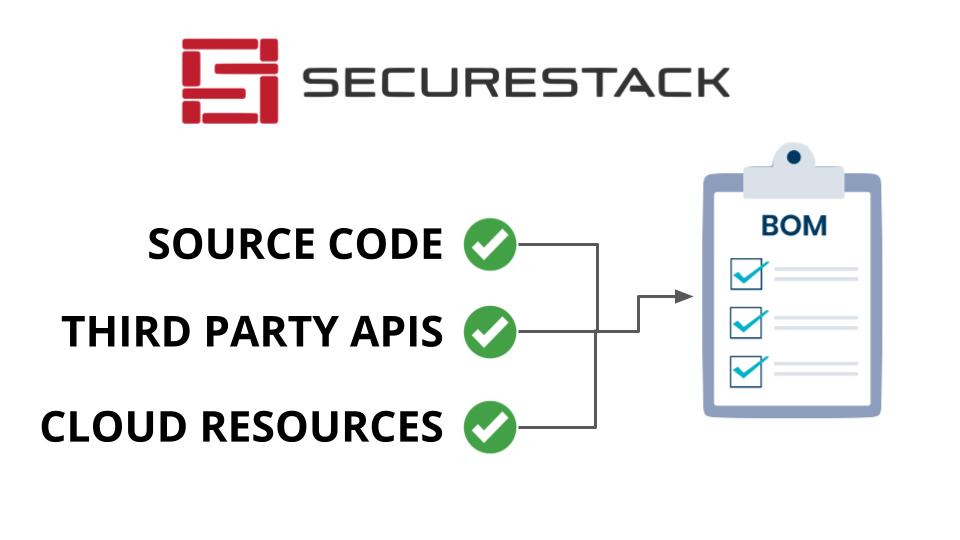
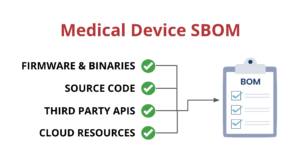
But modern applications are complex and include dependencies outside of the libraries that traditional SBOMs cover. Modern apps use multiple languages, third-party APIs, cloud-native services, and a lot more. Unfortunately, most SBOMs don’t address any of these additional dependencies or the vulnerabilities in them either. So we need to expand the idea of an SBOM to include all of the other resources and dependencies in
The government gets involved
Risks against the software supply chain are increasing. One of the problems historically has been a lack of visibility into how your vendors or partners create the software products you consume. The Solarwinds hack and the ongoing struggles for package managers like NPM prove that this part of our ecosystem needs better protections.

The Biden administration passed an executive order in 2021 entitled “The Executive Order on Improving the Nations Cybersecurity”. This executive order requires that any companies wishing to sell to the US government must meet SBOM requirements.
The UK government is thinking about how to create supply chain protections including SBOMs. The UK government is seeing opinions and looking to build a working group which you can read about here.
It is reported that the Australian government is going to mandate SBOMs for critical infrastructure organizations later this year. This will be a multi-stage process and will eventually mandate SBOMs for organizations of a certain size or in specific industries. This is an important step and will force many Australian organizations to learn about and implement SBOMs.

What’s in an SBOM?
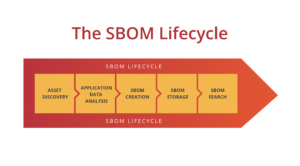
This is a tough question because not all SBOM tools agree on what should be in an SBOM. At its simplest, an SBOM is a list of all the different component parts of an application. So think of this as an index of all the dependencies built from a package manifest file. That’s really pretty simple and doesn’t really offer any additional functionality or benefit of simply using the package manifests themselves to derive this information. This is why most modern SBOM specifications include more info than just the package manifest. Things like the dependencies of a package should be understood and cataloged too. Many developers don’t realize how many additional pieces of software are being pulled into their projects because of dependencies, so this function is important.
I think most modern SBOM specifications agree on many things that should be in an SBOM. This typically includes several types of information about each component:
- Component name
- Supplier or vendor of the component
- Software license type
- Component version number
- Known vulnerabilities for component
- Transitive dependencies to other software
Defining these core data points about each application composition object means that engineering teams are in a better place to be able to mitigate or remediate issues in these components. Tracking this information over time means that a properly built SBOM will catch and make visible any changes that can adversely affect the application.
How do you create an SBOM?
Because there are several different formats for SBOMs organizations will need to make a decision on which they will support internally. Or, alternatively, they will need to have the right data in place to create any format they are asked for.
Unfortunately, there is no consensus on what an SBOM should look like or include. There are LOTS of suggestions, and vendors describing their way as the only way to create and handle SBOMs. The reality is that there are at least 3 different formats for SBOMs:
It’s important to note here that the SBOM specification or format, and the tool that is actually creating the SBOM are totally different. The former is the agreement of what should go into an SBOM and the latter is what is actually *put* in the SBOM.
Use Cases for SBOMs
The traditional use case for a SBOM is to provide a list of ingredients for an application. Typically, a software engineering team will own that use case and create SBOMs to store them for future reference. However, the idea of what a SBOM is has evolved. SBOMs have become less of a point-in-time snapshot and become more dynamic. SBOMs should be generated everytime an application is built and deployed. This allows organizations to track how their applications are changing over time with more granularity.
Engineering teams and security teams will have different use cases depending on what those teams roles are. In my conversations with security architects, their need for SBOMs is different. One of the best infosec use cases will involve giving infosec teams a searchable index of all applications so they can search it anytime there is a new software vulnerability disclosed.
Remember back in December of 2021 when the log4j vulnerabilities went public and the world freaked out right before Christmas. Teams spent days searching for applications that had log4j in them. Imagine instead if you had a central repository of SBOMs and could simply search them for log4j and get back a concise list of where log4j was used and what version it was. I can tell you from personal conversations I’ve had that would have saved thousands of hours of work by security and engineering teams globally.
SBOMs will evolve to become “Application Bill of Materials”
Software bill of materials (SBOMs) are a great way of capturing the software components and libraries that an application uses at a specific point in time. This gives the consumer of the software assurance that it is secure and built well.
Unfortunately, SBOMs don’t really capture the complexity of the modern application as those applications use multiple languages (monorepos, SSR), new types of infrastructure (Kubernetes, containers, serverless), third party services (Auth0, Stripe, analytics) and use cloud native resources from AWS, Azure and others. So we need to expand the idea of an SBOM to include these new components and evolve into an “Application Bill of Materials” or ABOM.

Paul McCarty
Founder of SecureStack
DevSecOps evangelist, entrepreneur, father of 3 and snowboarder
Forbes Top 20 Cyber Startups to Watch in 2021!
Mentioned in KuppingerCole's Leadership Compass for Software Supply Chain Security!