Address software supply chain risk with ABOM
What’s in your app? SecureStack provides visibility by building your application BOM automatically every time you deploy your application. We analyze the application’s source code and public cloud stack and include all necessary components in the BOM.
SecureStack sniffs out all your app components and automatically builds comprehensive BOMs
Our ABOMs are:
* Automated from CI/CD
* Centrally stored & managed
* Easily searchable
SecureStack BOMs provide real business value
After struggling during the Log4j incident organizations need a way to quickly mitigate future supply chain risks. SecureStack provides immediate business value by giving those orgs the ability to quickly identify where application components are and whether they are vulnerable. We provide automated BOM scanning and a built-in “BOM Explorer” which acts as the central source of truth for application composition.
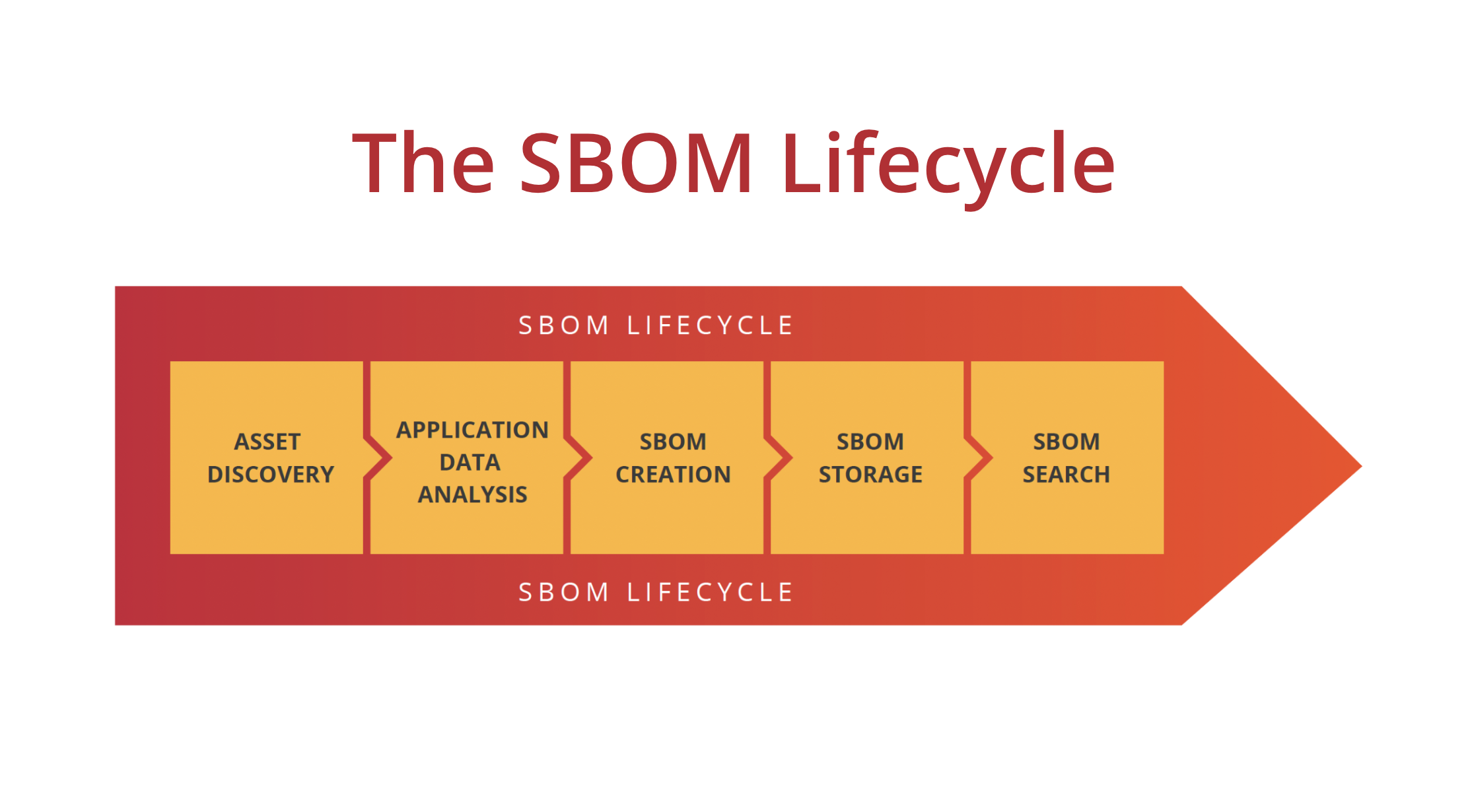
Automated BOM technology
SecureStack makes it super easy to implement a successful BOM program by automating the collection of data required to build BOMs. We do this using several unique scanning technologies. The end result is you get BOMs without having to spend weeks inspecting source code.
Check out our interactive tour!
Native CI/CD integration & automation
SecureStack runs natively in your CI/CD pipeline and automates the creation of a BOM with every deployment. SecureStack supports GitHub, GitLab, Bitbucket, AWS CodeDeploy, Azure DevOps, CircleCI, and dozens of other platforms.
Know what’s really in your applications
Our platform helps your teams understand what is in your applications. SecureStack analyzes source code, cloud stack, and third-party dependencies so you can know exactly what versions are running where.
Search your applications for specific components
Imagine if back in December 2021 when the Log4j vulnerabilities were published if you could quickly find out if you had a problem or not? Imagine if you could simply query a centralized BOM repository and find out where all log4j implementations were and what versions they were?
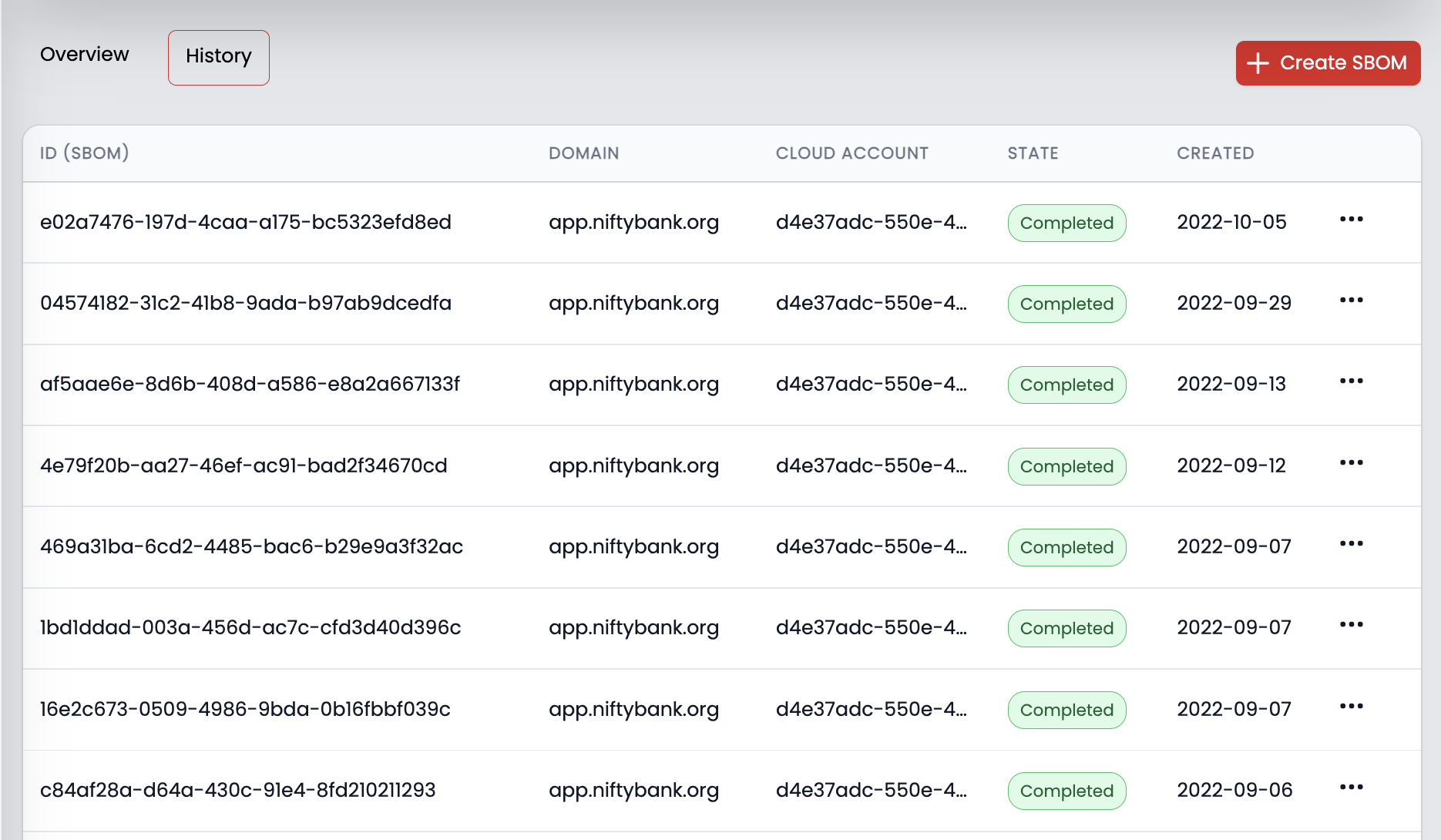
BOM centralized management
SecureStack gives your team a central place to store, manage and interact with your BOMs. You can download and interact with your BOMs at any time, and if a partner or auditor wants verification that you are producing BOMs you just point them to SecureStack.
How is SecureStack Different?
Made By Developers - For Developers
Bloodhound is the world’s first security platform built by developers, for developers.
Boost your development velocity
Continuous improvement to achieve a faster time to business and shrink your app attack surface by up to 70%.
Easily embed our unique git-centric tools
Into your existing development processes.
Asset discovery and attack surface mapping
Find and fix vulnerabilities, fast and without you needing to become a security expert.
Achieve peace of mind
Provide a sanity check on your deployment.
Test and compare your development, staging and production environments
To quickly find critical differences and understand ways to fix high priority defects.