
SecureStack adds AWS service detection to Project Discovery Nuclei
We want to encourage this dynamic community, so we are excited to announce that as of June 1, 2023 we will offer a completely free version of our platform. That free account will come with 20 analyses a month, and support all of our scanning technologies: web, cloud, code and secrets.

SecureStack Sign Up
Sign up for a free trial of the SecureStack platform. It comes with 20 monthly analyses & supports all of our web, cloud, code & secret scans

Confluence-Aggedon! Atlassian Confluence plagued by two CVSS 10 CVEs!
Two critical severity CVE’s were announced in October for the popular collaboration platform Atlassian Confluence. The first bug, CVE-2023-22515 was announced on October 4th, and classified as a CVSS 10! CISA published a CyberSecurity Advisory on October 5th which was...

SecureStack Community Edition Is Free!
We want to encourage this dynamic community, so we are excited to announce that as of June 1, 2023 we will offer a completely free version of our platform. That free account will come with 20 analyses a month, and support all of our scanning technologies: web, cloud, code and secrets.
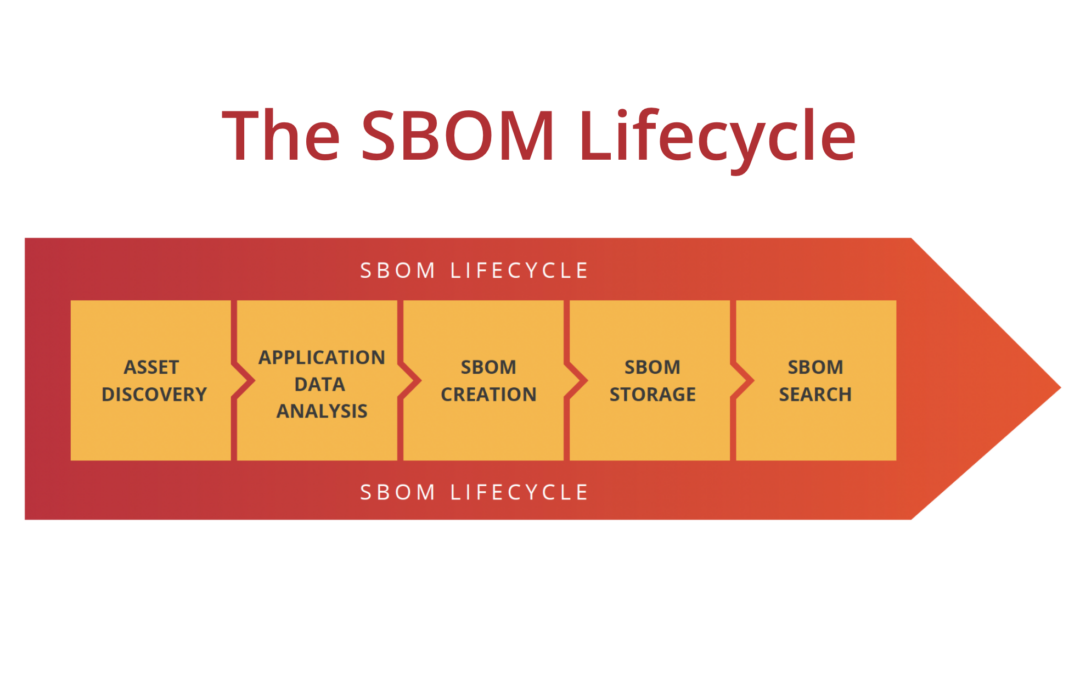
Software Supply Chain Security
Software supply chain attacks have grown exponentially over the last three years: malicious packages, package manager corruption, continuous delivery pipeline attacks, dependency confusion, zero days in open-source software and more. This is driving many...

New FDA Requirements for Cybersecurity
The FDA has released new cybersecurity regulations for medical device suppliers The Food and Drug Administration (FDA) has announced that medical devices must now meet specific cybersecurity guidelines. Cyber-attacks against healthcare organizations increased by 74%...
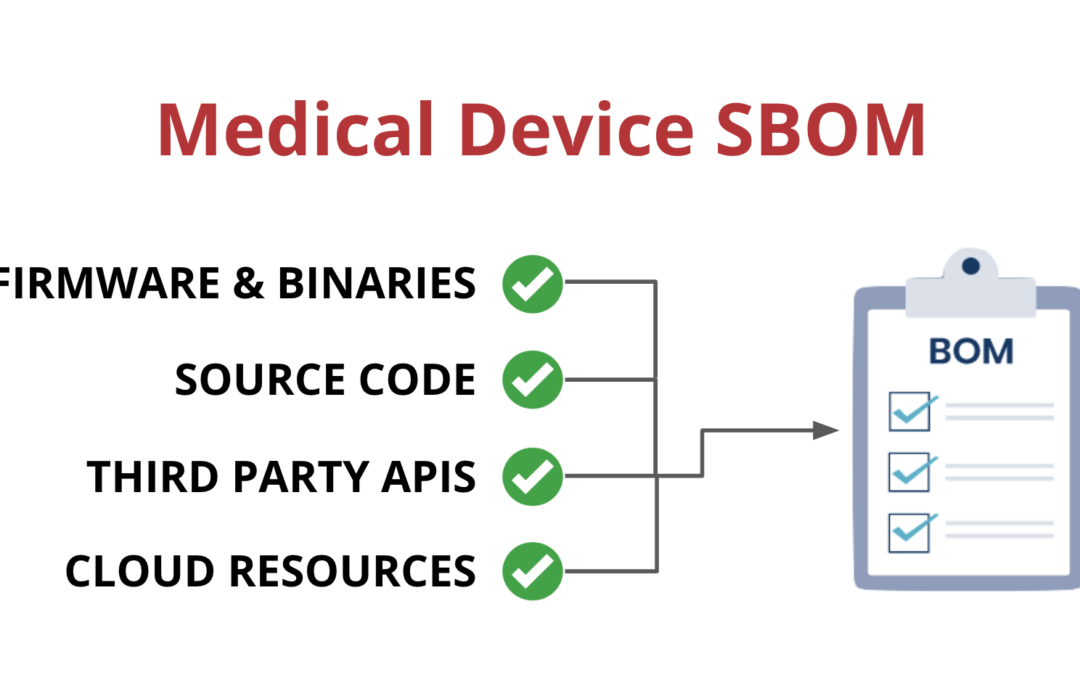
Medical Device Software Bill of Materials
Cyber attacks on medical devices are increasing Cyber-attacks against healthcare organizations increased by 74% last year, and attacks on the software supply chain have increased an average of 610% per year since 2020. These attacks can take various forms that attack...
Check out our interactive demos
Want to see more SecureStack demos? Software Supply Chain VisualizationCreate an SBOMContinuous ComplianceConfigure Azure DevOps Paul McCarty Founder of SecureStack DevSecOps evangelist, entrepreneur, father of 3 and snowboarder Forbes Top 20 Cyber Startups to...

Complete security coverage for Azure DevOps
SecureStack is excited to announce that we now support Azure DevOps through the use of our native Azure Pipelines templates! SecureStack provides comprehensive security coverage with our brand-new Azure DevOps integration. Our customers asked us to support Azure...
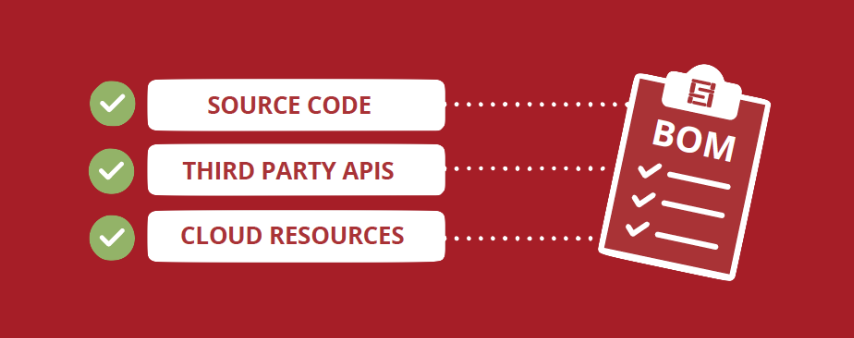
Comprehensive SBOM
Comprehensive SBOMs can help address software supply chain risks One way to address the risks inherent to the complex applications we are building is to use "Software Bill of Materials" also known simply as "SBOM". At its simplest, a SBOM is a list of all the...
