What is the Log4J vulnerability?
Log4j 2 is an open source Java logging library developed by the Apache Foundation. It is a key building block which is reused to provide logging functionality to help system developers troubleshoot in a large number of applications globally.
Many forms of enterprise and open-source software, including cloud platforms, popular apps such as Minecraft, websites and email services, use Log4j; it is a dependency for many services.
The Log4Shell incident explained
On 9th December 2021, the project disclosed the vulnerability publicly on GitHub. They identified that an exploit in the popular Java logging library log4j (version 2) has been discovered, resulting in unauthenticated Remote Code Execution (RCE), by logging a certain string.
Common Vulnerability Scoring System (CVSS) rated the vulnerability as a critical 10/10 severity. Given how common this library is, the impact of the exploit (full server control) as well as how easy it is to exploit; the impact of this vulnerability is quite severe. The critical vulnerability (CVE-2021-44228) exists in certain versions of the Log4j library. It’s termed “Log4Shell” for short.
A malicious cyber actor could exploit this vulnerability to execute arbitrary code and compromise systems and networks. Thousands of devices around the world connected to the internet could be at risk.
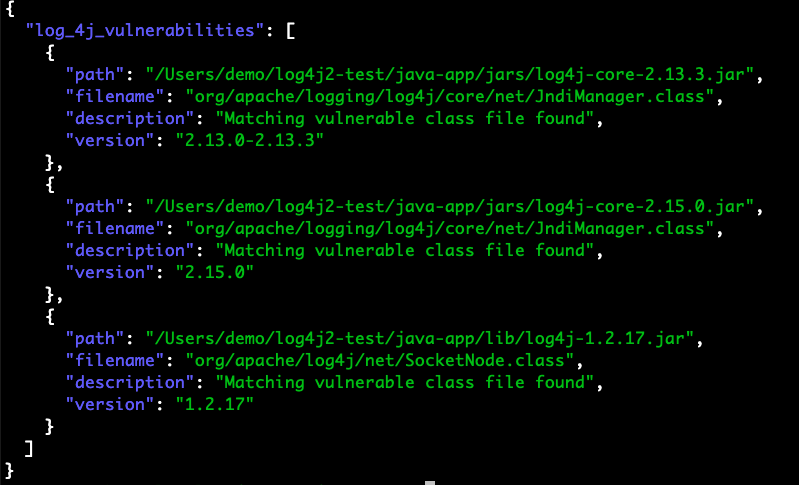
What vulnerabilities of Log4J should I check for?
SecureStack offers users an easy solution to identify if you are at risk, simply scan your application and SecureStack will identify within 4 minutes, all affected versions of log4j in the application stack (as well as additional vulnerabilities, misconfigurations and issues you may have). Once the application issue is identified, a simple step-by-step solution will be provided to mitigate the risk.
Alternatively, System administrators should check potentially vulnerable servers for outbound traffic to hosts outside the local network which may indicate communication with command and control nodes or traffic to internal hosts indicating attempts of lateral movement.
Requirements for an exploitation
- A server with one of the vulnerable log4j versions listed below:
- 2.0-beta9 to 2.12.1
- 2.13.0 to 2.14.1
- 2.15.0-rc1
- 2.16.0 to 2.17.0
- An endpoint with any protocol (HTTP, TCP, etc), that allows an attacker to send the exploit string.
- A log statement that logs out the string from that request.
Find out if your application has a vulnerable log4j version by scanning your application here.
What’s a CVE and how does that relate to log4j?
CVE is short for “common vulnerabilities & exposures” which basically is a way to describe a specific type of vulnerability in a standard way. Each specific vulnerability gets its own CVE number that starts with the year it was added to the CVE database and then a five digit number.
The log4j class of vulnerabilities is large and multifaceted so there are actually 5 CVE’s related to the log4j family of vulnerabilities:
- CVE-2021-44228
- CVE-2021-4104
- CVE-2021-44832
- CVE-2021-45046
- CVE-2021-45105
Find log4j vulnerabilities with SecureStack
The SecureStack platform is the only solution in the world that can help you find log4j vulnerabilities in your source code, cloud provider, and by scanning your running web application. It’s super easy to find and then mitigate log4shell with one solution.
Create Free Account