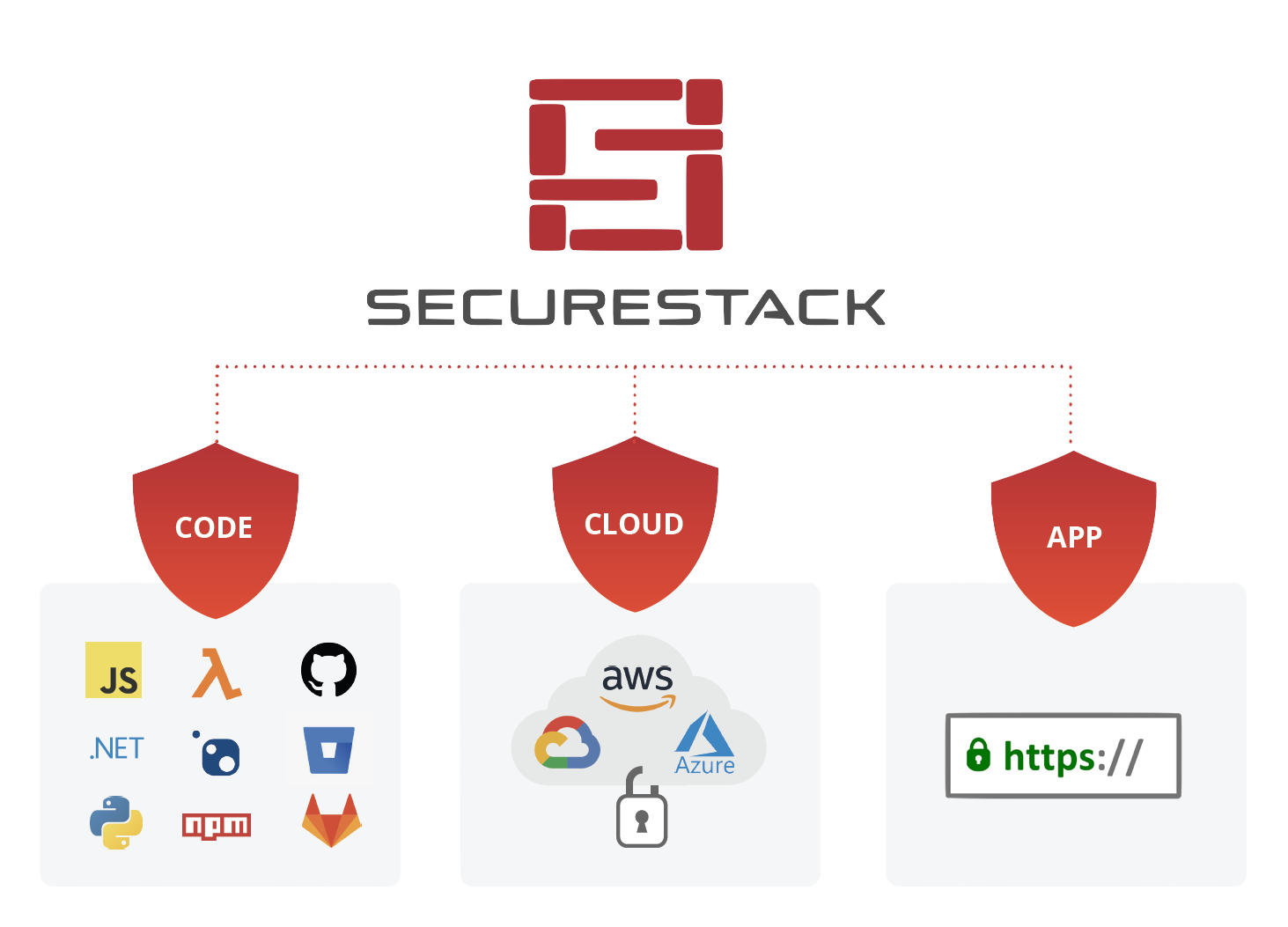
Want security coverage for your SDLC?
Integrations for git, CI/CD, build, and cloud native resources
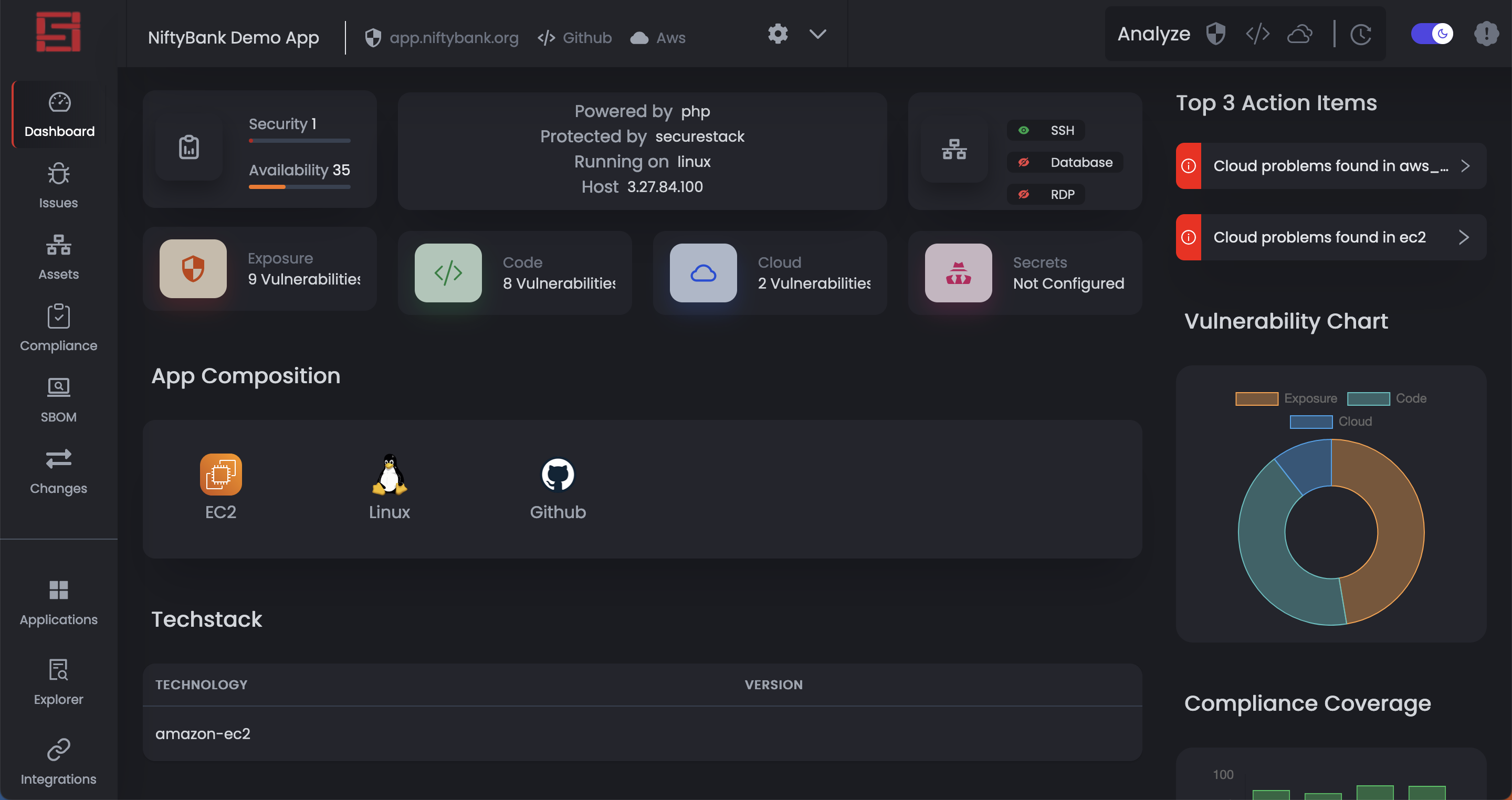
Monitor All Your Web Applications From One Place
One dashboard to rule them all! Data from source code scans, vulnerability scans, credential scans, cloud misconfiguration analyses all go into one dashboard. Alerts are sorted by actual criticality for the target application, not by what some opinionated vulnerability database says.
Our innovative “DevSecOps Compliance” technology does the work for you.
SecureStack continuously analyzes your running web applications, CI/CD processes and cloud resources for security issues. We then map anything we find to the compliance frameworks that you care about. SOC2, ISO27001, Australian ISM, NIST 800, NIST SSDF and CIS are all supported out of the box.
Data from source code, cloud stack & application attack surface combined
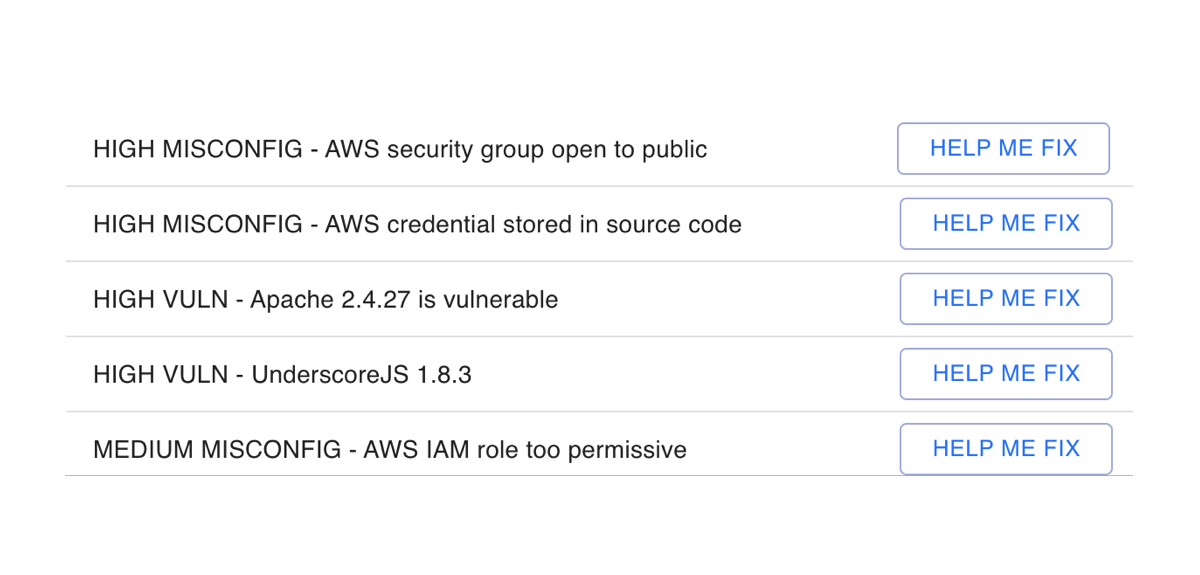
SecureStack combines data from all three sources and prioritizes what you need to address first.
Then we help you fix it.
Hunt Threats You Never Could Before
Credentials, third party libraries, API keys and secrets, misconfigurations in AWS and Azure cloud resources. Gain visibility into all the public web assets for your organization, all from one tool.
Embed Fixes Into Your Existing CI/CD Processes
With triggers in the CI/CD pipeline, security teams can be notified automatically when disruptive changes are made to applications and know how to mitigate those issues.
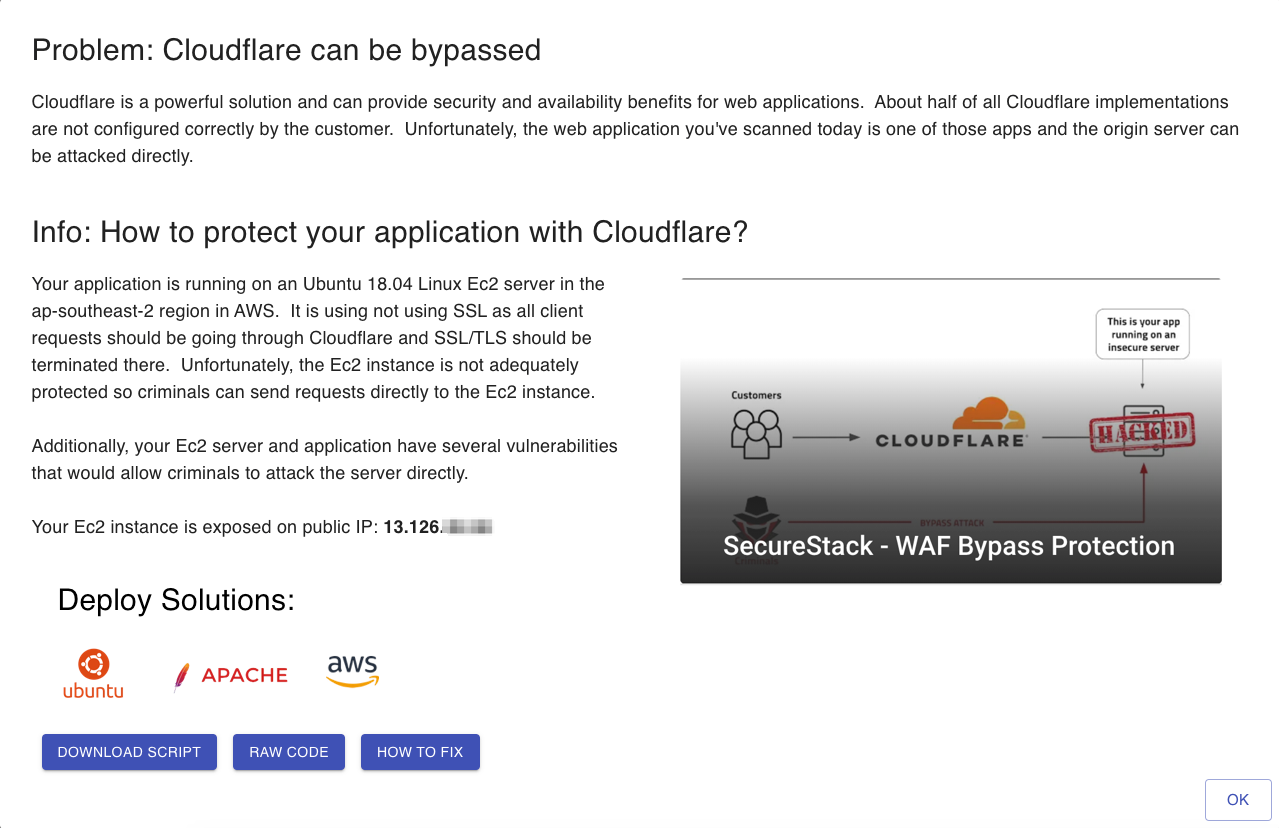
Access Insights & Solutions
Gain deeper insights around why a specific control is important and how our guardrails will guide you and help your application be more secure.
How is Bloodhound Different?
Made By Developers - For Developers
Bloodhound is the world’s first security platform built by developers, for developers.
Boost your development velocity
Continuous improvement to achieve a faster time to business and shrink your app attack surface by up to 70%.
Easily embed our unique git-centric tools
Into your existing development processes.
Asset discovery and attack surface mapping
Find and fix vulnerabilities, fast and without you needing to become a security expert.
Achieve peace of mind
Provide a sanity check on your deployment.
Test and compare your development, staging and production environments
To quickly find critical differences and understand ways to fix high priority defects.