When the news came out about the Log4J vulnerability back in December 2021, the technology world was taken by absolute surprise. Companies from startups to enterprises were all asking the question “are we vulnerable”? For some businesses this was an incredibly difficult question to answer; with the advent of microservices, some companies needed to search for the Log4J vulnerability across hundreds of repositories and update their dependencies as soon as possible. Some companies now face a similar conundrum with the VM2 nodejs package vulnerability.
VM2 nodejs package vulnerability
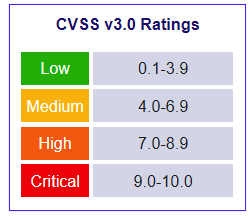
On the 28th of September, an advisory was published by Github about a 10/10 vulnerability in the VM2 node package. A CVSS score of 10 is almost unheard of and represents a vulnerability that is currently being exploited and is very easy to exploit. SecureStack makes use of nodejs in many of our applications, so it was prudent that we investigate this vulnerability and ensure that we avoided using a vulnerable version of VM2 and have our applications open to attack. It’s important for us to note that while we may not have VM2 in any direct dependencies our application’s sub-dependencies may have had it and if it did, we needed to update to a version that has been patched. To do this we made use of The SecureStack dependency explorer.
The SecureStack explorer
Companies making use of SecureStack have access to two important products in situations like this: A software bill of materials (SBOM) and our dependency explorer. When customers have SecureStack in their CI/CD pipelines they are able to generate SBOMs for every release they make whether that might be in a development release or a production release. This enables incredibly up-to-date information about their packages and vulnerabilities available at our customer’s fingertips.
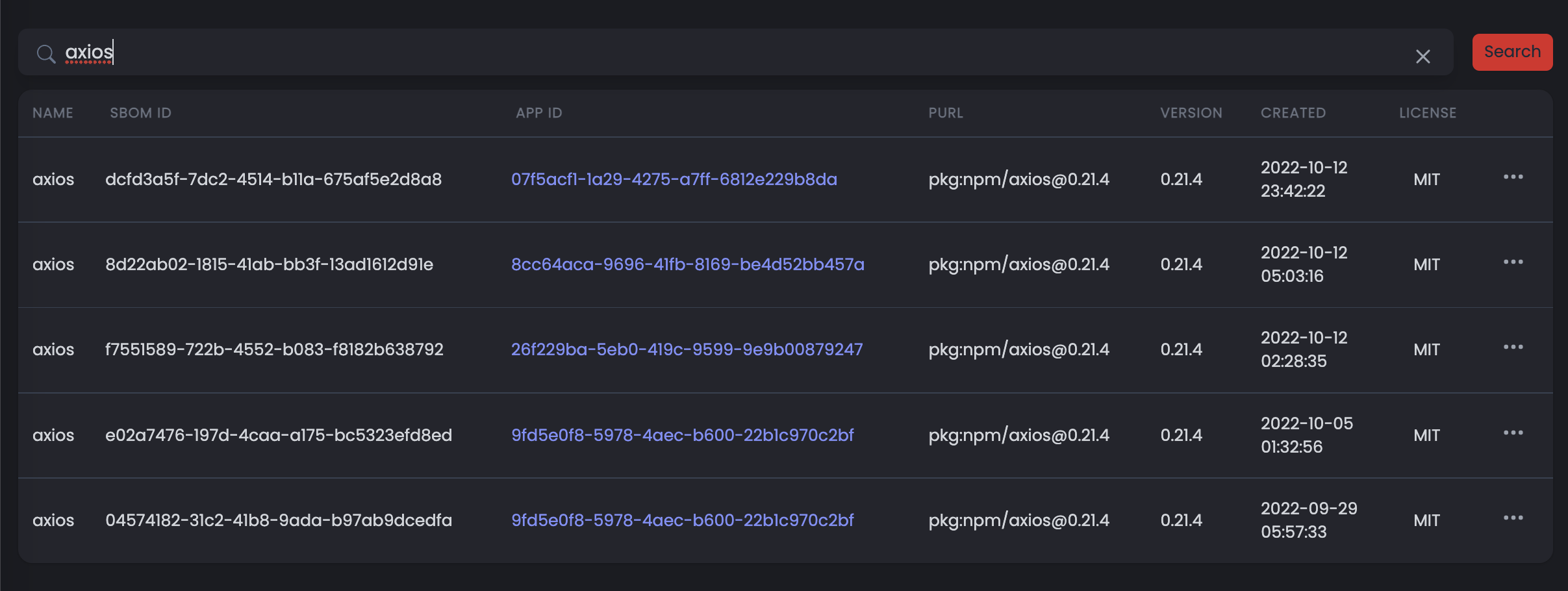
Here’s what the explorer looks like:
You can see when we search for axios it shows the various applications that contain packages like the axios package we’re searching for in the above screenshot. Importantly, it also shows what version of the package is in use and when that application was last analysed. This allows you to see if it’s been too long since your application was analysed and therefore be providing out-of-date dependency information.
So using the explorer, we were able to determine that we were in fact not using the VM2 dependency anywhere in our applications and were therefore safe from this critical vulnerability.
SecureStack for keeping your organisation secure
SBOM generation and the dependency explorer are just 2 of the many features SecureStack has on offer for our customers to help keep their applications secure.
If you are wondering what vulnerabilities your application might have or if you too are using the vulnerable VM2 package: sign up for a free account with SecureStack and get access to 20 free analyses for your applications.