SecureStack adds AWS service detection to Project Discovery Nuclei
SecureStack and Project Discovery partner to help bring AWS service detection to Nuclei!
We are super pumped to announce our new partnership with Projectdiscovery.io!
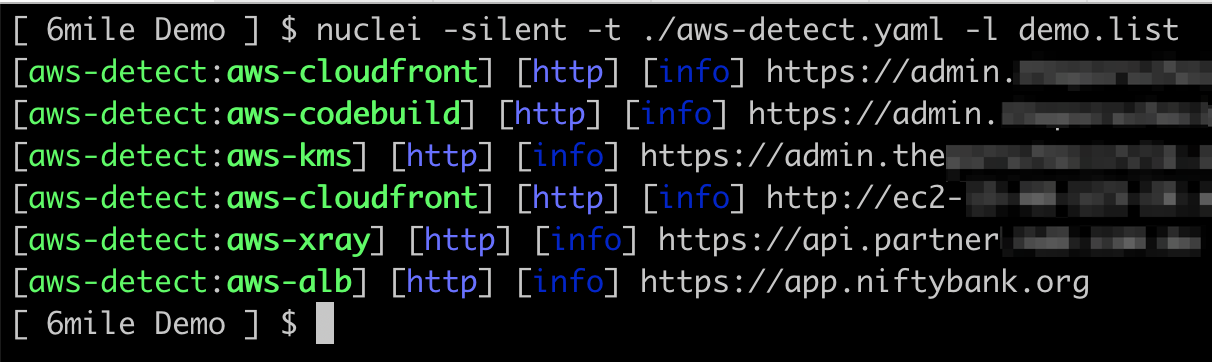
SecureStack has developed a new Nuclei template for AWS service detection. This allows you to use Nuclei to identify AWS services that an application is using.
Founder and CEO Paul McCarty says “This Nuclei template started out as a set of internal functionality in the SecureStack platform, but over the last year we realized that it’s important for people who use open source tools like Nuclei to have this visibility as well, so we ported our detection into Nuclei templates.”

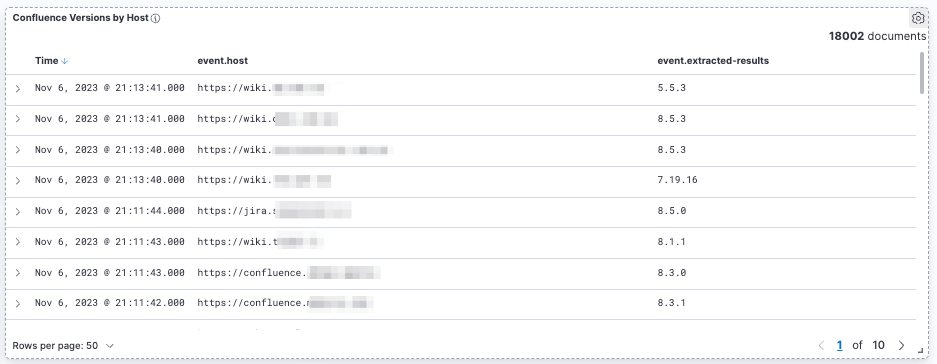
Identify 10 different services in AWS applications
This new template will quickly scan a target and identify what AWS services are being used via standard HTTP requests. The AWS services that this new template identifies include Cloudfront, EC2, AppSync, ELB, Codebuild, DynamoDB, S3, API Gateway, KMS, WAF, and Xray.
Use Cases
The template is designed for the security and engineering teams protecting the cloud environment
- Visibility into your AWS services – know which AWS services are part of different application environments.
- Identify the underlying services operating your WAF and CDN providers – If you are using Cloudflare, Akamai, Imperva or other similar services, you often don’t know what cloud services are being used as the WAF obfuscates service information
- Understand and safeguard your AWS environment – you know what’s exposed to the internet and what’s not, so you stay one step ahead of potential threats and minimize the risk of security breaches
- Bug bounty researchers and penetration testers – This template lets you quickly scan large numbers of assets for AWS services for in-scope bounty programs.
PJ Metz from Projectdiscovery.io says “Paul’s template is extremely valuable in reconnaissance while working on a bounty or pentesting; knowing your attack surface is probably the most important step since you can’t protect/attack what you don’t know exists. ”
You can check it out as part of the latest Nuclei template release at https://github.com/projectdiscovery/nuclei-templates
About SecureStack
At SecureStack, our mission is to provide a fully integrated platform that enables engineering and security teams to collaborate seamlessly. This partnership with Projectdiscovery.io is the next step towards this goal.
Take your AWS security to new heights by downloading our Nuclei at https://github.com/projectdiscovery/nuclei. Nuclei will automatically download the latest templates, including the new aws-detect.yaml template.
Stay tuned for more updates as we grow the vulnerability detection capabilities of the SecureStack platform.

Paul McCarty
Founder of SecureStack
DevSecOps evangelist, entrepreneur, father of 3 and snowboarder
Forbes Top 20 Cyber Startups to Watch in 2021!
Mentioned in KuppingerCole's Leadership Compass for Software Supply Chain Security!