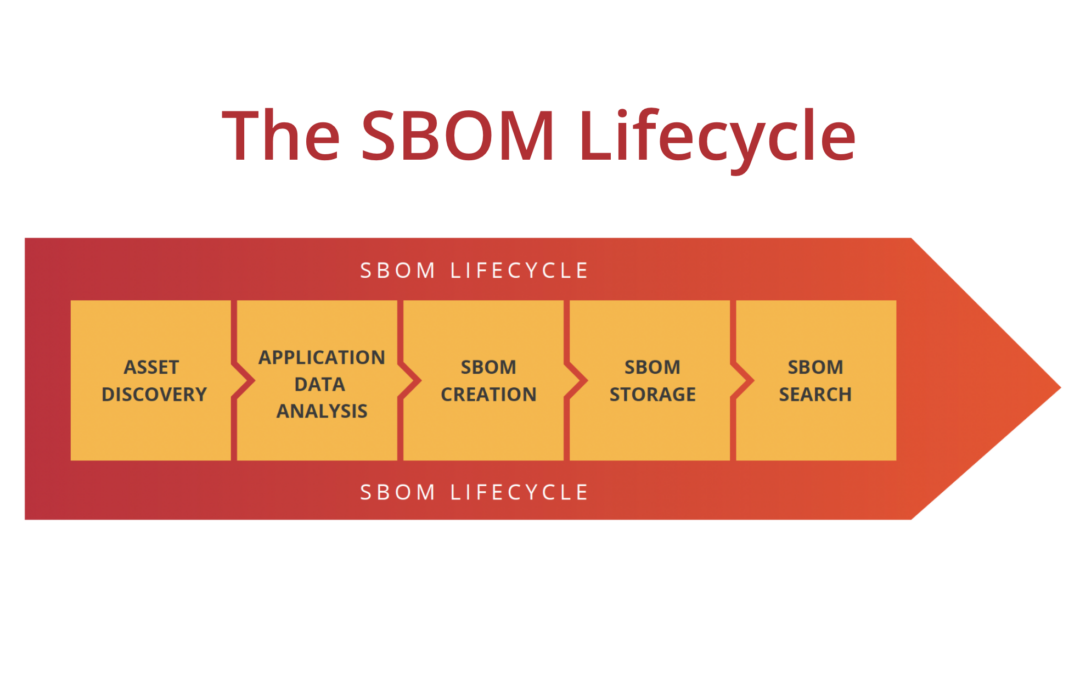
The SBOM Lifecycle
Software supply chain attacks have grown exponentially over the last three years: malicious packages, package manager corruption, continuous delivery pipeline attacks, dependency confusion, zero days in open-source software and more. This is driving many...

Staying secure from the VM2 vulnerability
When the news came out about the Log4J vulnerability back in December 2021, the technology world was taken by absolute surprise. Companies from startups to enterprises were all asking the question “are we vulnerable”? For some businesses this was an incredibly...
SecureStack is sponsoring NDC Sydney 2022!
SecureStack is sponsoring NDC Sydney 2022. NDC is a global high-end software developer conference. Come and see us at booth #8 on the main floor. We will be giving away an awesome LEGO set!

What is a SBOM?
One of my friends messaged me on LinkedIn today and asked "What is this SBOM you keep talking about?" I realized that he's right and I should probably explain what an SBOM is. So, let me start by defining the acronym: SBOM refers to a "Software Bill of Materials"....

SecureStack Organizations is now available
The SecureStack team has been working on this release for months as we were introducing several new concepts which meant we had to rearchitect many parts of the platform. But most importantly we are introducing several new pieces of functionality in this...

LastPass hacked and source code stolen
LastPass was hacked and their source code was stolen. What can we learn from this? LastPass, just sent an email to its customers saying that it has been hacked. Again. LastPass has publicized that it's been hacked at least 4 times: in 2011, 2015, 2021, and now in...

How to enforce HTTPS on your web application
Enforcing HTTPS is a lot harder than most people make it seem So, lemme break this down into the 7 (yes 7!) different things you are gonna need to have configured to meet the requirement in the top paragraph: create the unencrypted "origin" service create a load...

Risky Business
Risky Business Podcast In this edition of Snake Oilers we'll be hearing from Google Security -- Anton Chuvakin is appearing on their behalf to talk more about how switching to its cloud-native SIEM actually makes sense now. Paul McCarty from SecureStack will be along...

Australian ISM – Guidelines for Secure Development
The Australian Cyber Security Centre (ACSC) is the arm of the government that provides guidance on how to improve cybersecurity in Australia. As part of this mandate, they have been producing a document called the "Information Security Manual" (ISM) since 2017. You...

Automate responses to security questionnaires!
Are you sick of filling out security questionnaires to meet some compliance or audit objectives? Most of the software engineers we talk to that have to fill these pesky forms out hate the process. Many of them say to us that they really want something that could...
