Comprehensive SBOM
Comprehensive SBOMs can help address software supply chain risks
One way to address the risks inherent to the complex applications we are building is to use “Software Bill of Materials” also known simply as “SBOM”. At its simplest, a SBOM is a list of all the different component parts of an application. This typically includes several types of information about each component: Its name, who supplied the component, what license it uses, the version number, any known vulnerabilities, and a list of all the component’s dependencies.
Application complexity is increasing
The reality is that modern applications are complex and dynamic, and therefore hard to secure. They use programming languages that run entirely in the browser, they talk directly to their dependencies on the internet and they use technologies like containers, serverless and public cloud. All of these bring their own challenges, so we need visibility into all these other application components and dependencies as well. What third-party APIs and public cloud components is it using? Is it using an identity provider like Auth0 or Cognito? What infrastructure is required to make the app run? All of these things need to be understood to really be able to better represent what is in an application and how to secure it.
Traditional SBOM tools do not produce accurate results
Most SBOM tools that exist right now, simply focus on showing customer the open-source libraries that they are using in their applications. Moreover, most SBOMs are stand-alone XML or JSON documents. By themselves these documents don’t provide much value. Even worse, most SBOMs are point in time generated and then never updated. So, these “static” SBOMs quickly become out of sync with the actual application they are supposed to describe.
Application complexity forces SBOM to evolve
The reality is that existing SBOM implementations are not accurately describing the applications they are supposed to represent. Instead, they represent a part of the application: open-source libraries. There is a drive within the industry right now to provide a better, more comprehensive SBOM that does a better job of describing the complex modern web apps that we are building. To do this, you need to use data from other sources than package manifest files.
What is a comprehensive SBOM?
As we said above, modern applications are complex and use components other than open-source libraries. These apps use third-party APIs, SaaS providers, and cloud-native resources, among other things. This data needs to be collected from the target application and used to provide a better more realistic SBOM.
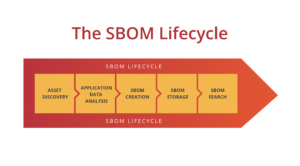
The comprehensive SBOM is a document that describes this type of application fully. Moreover, a truly comprehensive SBOM will also be up to date and searchable. Let’s drill into this a bit more.
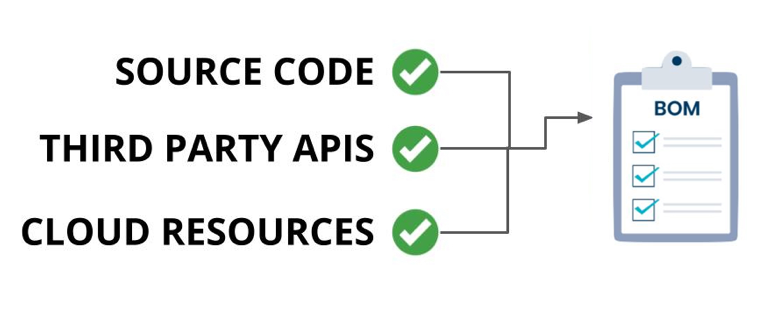
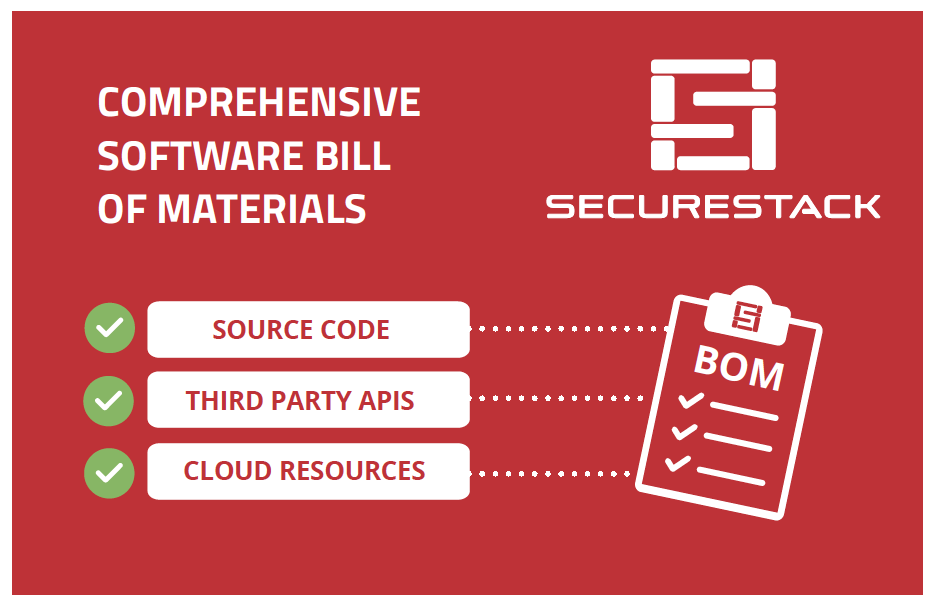
SBOMs need three things to be comprehensive:
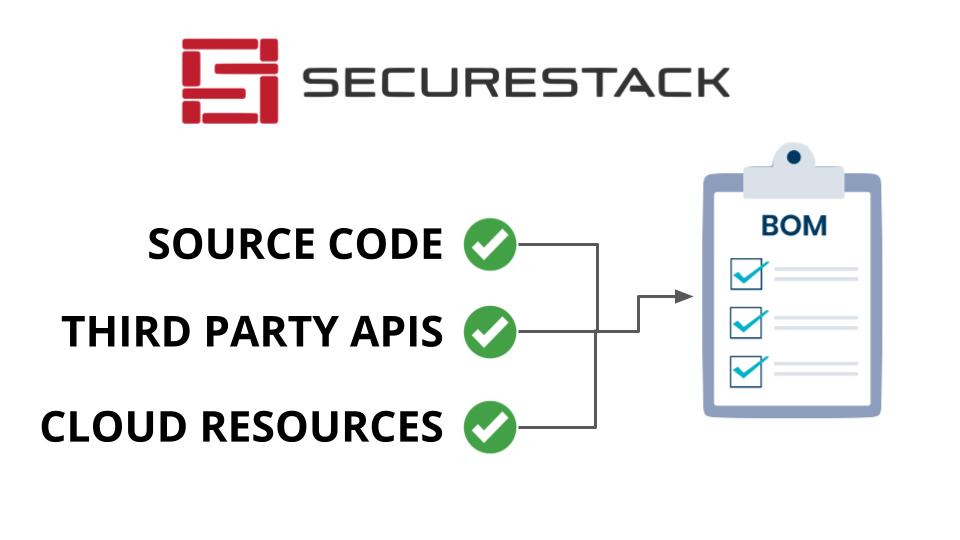
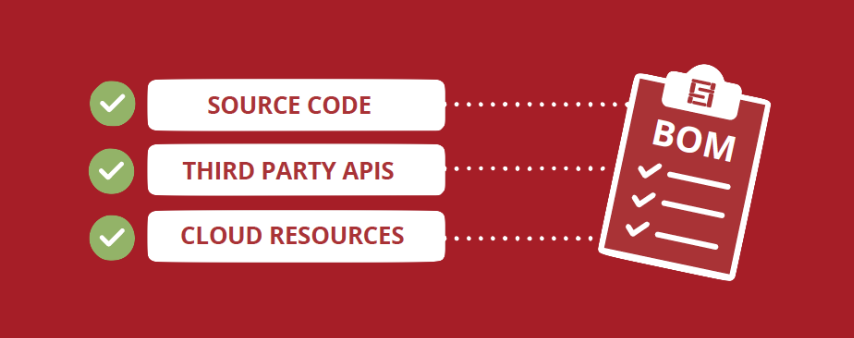
- Data from source code, third-party APIs and SaaS dependencies as well as any cloud-native and identity providers that the application requires.
- Timely. SBOMs need to truly represent what the application looks like and that means that any time there is a change to the application the SBOM needs to be updated. The only thing worse than no SBOM is an incorrect SBOM.
- Finally, SBOMs need to be searchable. There’s no point to generating SBOMs if all you do with them is store them somewhere. What happens the next time there’s a Log4shell-type incident? You need to be able to search your SBOMs so you can find vulnerable technologies quickly.
The business value
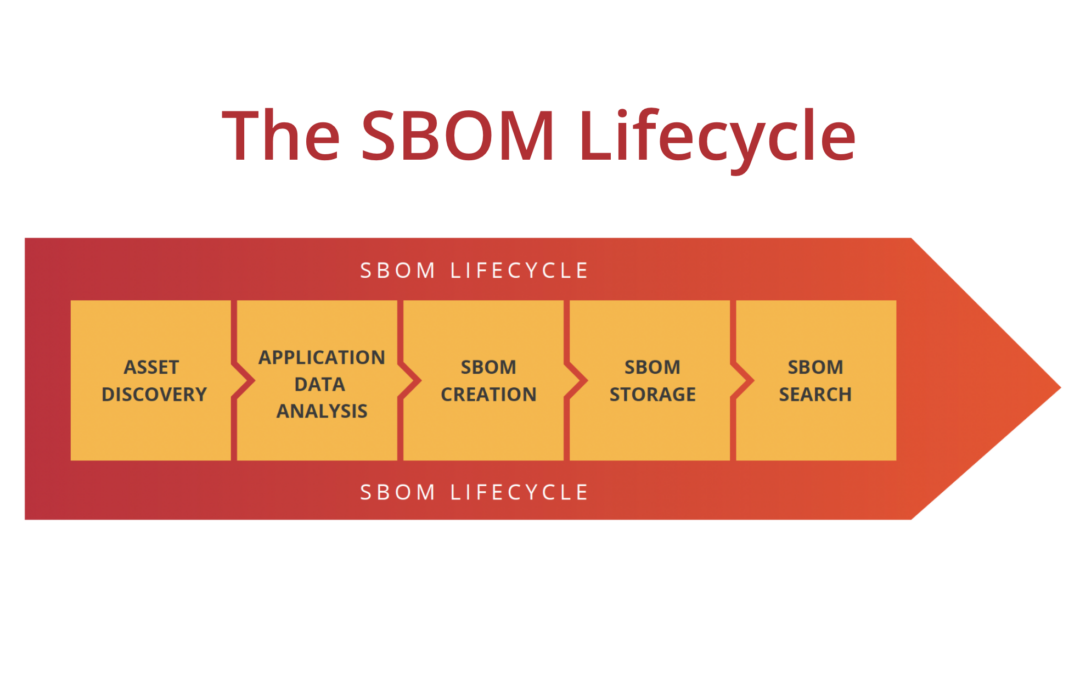
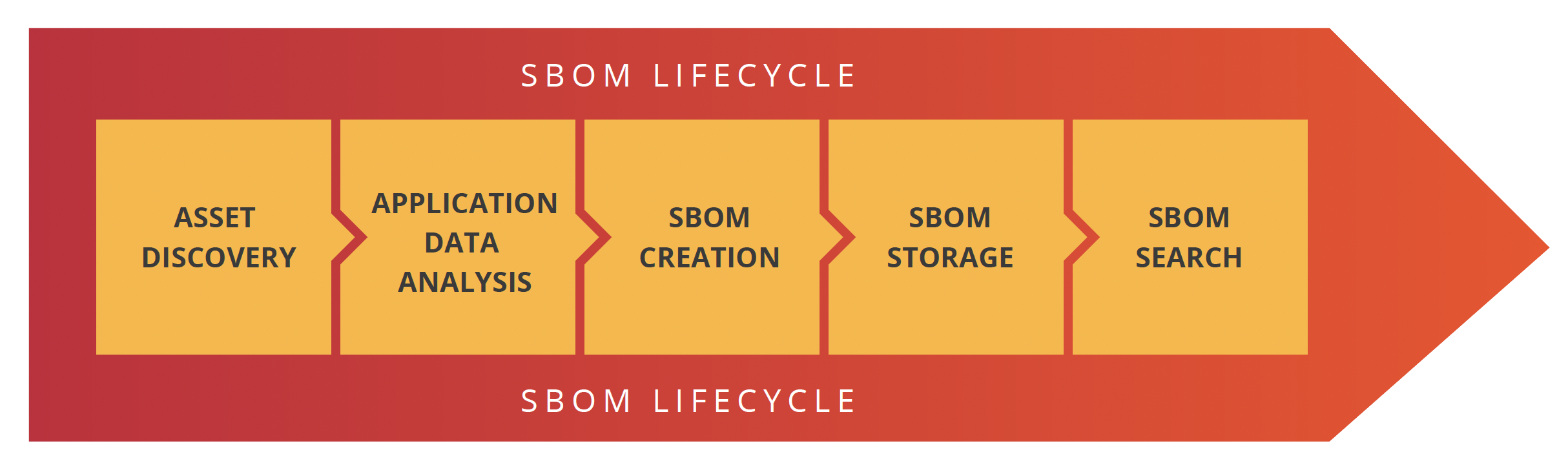
Building a complete SBOM lifecycle can be a challenge, but in the end, the value that it provides to organizations is enormous. Simply having the ability to quickly find all the software and application components in your estate of apps is huge. But even better, being able to query that data for vulnerable components could save organizations millions of dollars in lost productivity.
Automated SBOM platform
SecureStack automates the whole SBOM process from end to end. Our platform delivers all stages of the SBOM lifecycle in a fully integrated solution that is incredibly easy to onboard. SecureStack integrates easily into your CI/CD pipelines and workflows so that SBOMs are generated, stored and made searchable, automatically. Because they are generated directly at build and deploy time you know that they are accurate and provide the most business value for your organization.
See how it works!

Paul McCarty
Founder of SecureStack
DevSecOps evangelist, entrepreneur, father of 3 and snowboarder
Forbes Top 20 Cyber Startups to Watch in 2021!
Mentioned in KuppingerCole's Leadership Compass for Software Supply Chain Security!