6 easy things to increase source code security
Enable MFA for SCM
Bitbucket, GitHub, and GitLab all support the use of MFA for logins. This simple security control means that there’s more than just a crappy password between your source code and attackers. Even better, if you use GitHub or Bitbucket or GitLab for SSO to other platforms the requirement to use MFA at login will propagate across automatically, providing security there too.
The obvious limitation with this method is that you are only going to get an MFA challenge when you log in, so doesn’t provide any security when you are actually interacting with code (pulls, fetches, clones, etc). That’s why the next option is particularly important.
Use SSH keys to interact with SCM
There are two protocols that are supported when you interact with source code in your SCM. The default is HTTPS which is encrypted but doesn’t offer any additional security. The other option is to use SSH for transport which requires SSH keys as it’s PKI based. This is significant as you can change, expire, and update your keys based on company requirements.
My team has gone even further, as we use an app that manages SSH private keys behind an MFA challenge. This means that each time we push code we get a challenge on our mobile devices. Combining this control with the first one (MFA) adds a layer of security that is very powerful. You can see how to add SSH keys to your GitHub account here.
Signed commits
When an engineer makes an important change to source code they will “commit” that code to version control so it’s protected. Unfortunately, by default git just keeps track of the author via the email address of the author which can be easily faked. If you want to verify that the person pretending to be linus@linux.org really is Linus Torvalds, then you need to sign your commits with GPG. It takes 60 seconds to set up and then can be easily automated so that every commit is signed. Find out how to sign commits here.
Scan your source code for vulnerabilities
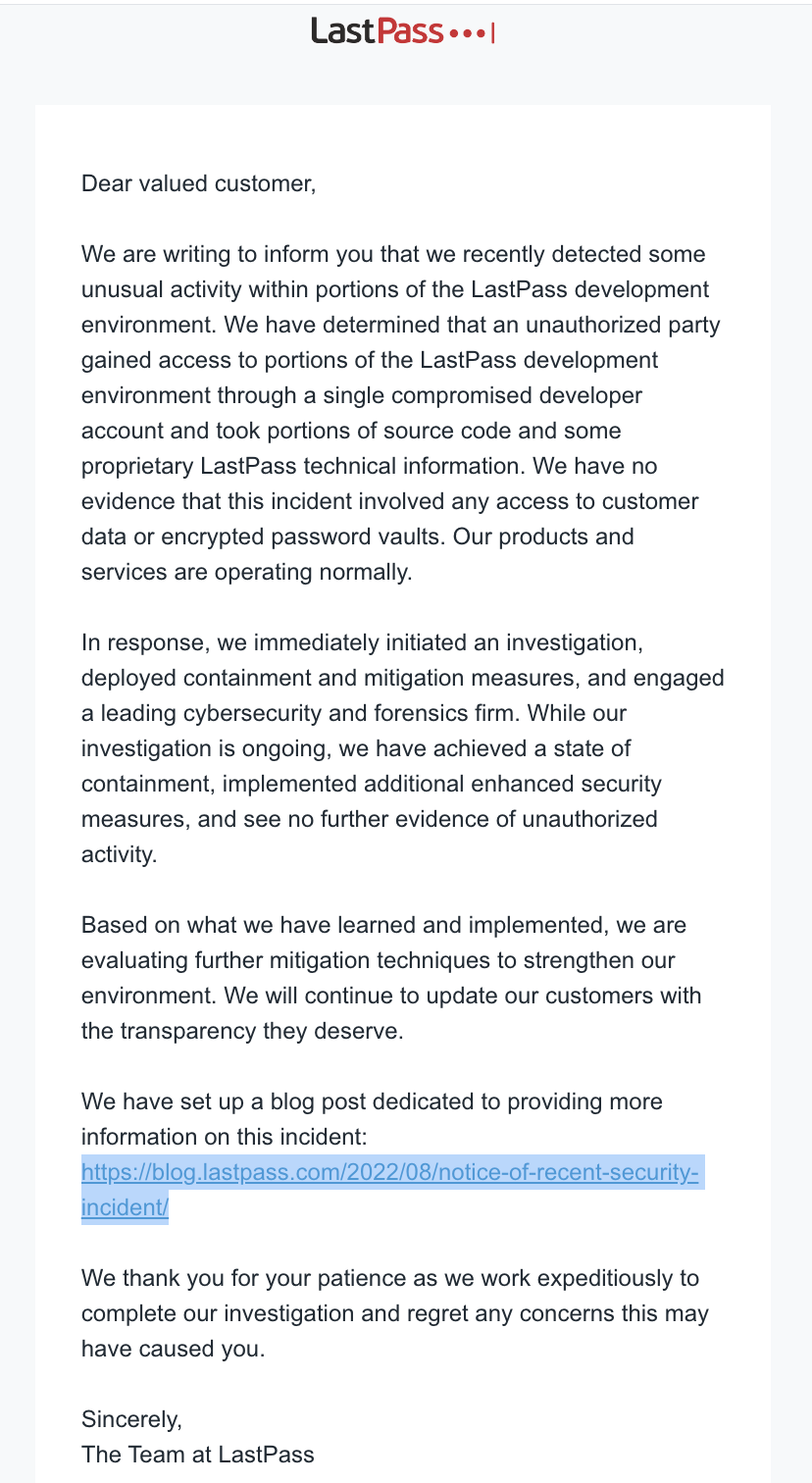
While this control wouldn’t have stopped the LastPass hack, it’s still a super important security control. Good engineering teams will use software composition (SCA), secret scanning tools, and static analysis (SAST) code scanning solutions in their local environments. It’s super important to scan source code for issues when it goes through your CI/CD pipelines, but it’s important to do on your developer’s laptops too. Git provides an automated function to do this when you commit code with something called a pre-commit git hook. Unfortunately, a lot of engineering teams are NOT running security tooling on their laptops so there is no way to stop security issues or malicious code from getting into the centralized source control system. Yes, you can eventually remove it there too, but it’s a lot harder to do than if you stopped it before it got there. I like to use the analogy of someone poisoning a city’s water supply. It’s a lot easier to stop them from pouring the poison into the lake than it is to take the poison OUT of the lake.
Sync your SCM provider to AD
One of the common themes I see is that enterprise orgs will use a cloud-based SCM like GitHub or Bitbucket, but not connect their active directory to it (usually because of cost). Because they aren’t linked, the users in the SCM platform must be managed separately. This causes challenges as users have to manage two separate sets of credentials, one for AD and one for SCM. It also means that accounts are often out of date with people still having accounts in SCM when they no longer work for the company. Onboarding, off-boarding, password resets, and everything else is more complicated in this scenario.
Security training for your software engineers
Because of the unique security challenges presented to developers, they need specialized security training. That’s why we use partners that teach how to create more secure code, but also how to secure the systems they use to manage the code. Reach out to me if you would like an intro to one of our partners that does this.