13 Security tips that might save your small business
UPDATED: October 6, 2022
Small businesses are a huge part of our economy
Small and medium businesses (SMB) account for 97% of all businesses domestically and employs 68% of Australians. SMBs are usually described as less than 50 employees, with $10Million of annual turnover or less.
This large part of our economy is not well suited for many of the sophisticated cyber attacks that now exist. They usually don’t have any IT employees and instead outsource the IT administration to Managed Service Providers (MSP) or IT consultancies. These same small businesses are the hardest hit by cybersecurity issues with 60% of SMB companies going out of business within 6 months of a cyber attack or data breach. Small businesses just don’t have the resources to fight and then contain a cyber event and they’re rarely prepared for the brand damage that will come from it and eventually stop trading. This is particularly true for ransomware attacks as often the important data can never be recovered. Imagine if this is your list of clients? Or your intellectual property? Or if you’re a graphic designer and all your images were suddenly unusable. You can see how this could kill some companies.
“If I knew then, what I know now…”
I saw this first hand as an IT consultant for many years. Before a breach customers would often say that it wasn’t worth paying the money to address existing security issues. This is common as SMBs typically don’t like paying for cybersecurity but are the hardest hit when it eventually happens. This paradox is not sustainable and we need to find inexpensive ways for SMBs and startups to uplift their cybersecurity.
This is even more important in a post COVID-19 world. Teams were moved to work from home (WFH) quickly and many smaller companies didn’t have time to sufficiently prepare for the cybersecurity challenges that this new world presents. I started writing this several months back, but this is a perfect time for me to publish.
13 tips for your small business
So, here’s my list in a roughly prioritized fashion. The emphasis is on simple security that non-technical people can use. These first eight controls (1-8) are implemented on the employee’s individual computer, or phone (or both). Numbers 7 and 8 need to happen on employee computers, phones AND any servers (physical or virtual) that the company owns.
1. Multi-Factor Authentication

The most important thing you can do
Before you do anything else install a multi-factor authentication (MFA) app on your smartphone if you don’t have one installed now. Then have all your employees do the same thing. I prefer Authy, but the Google Authenticator application is probably the most common. Being a Michigan boy, I have to mention the Duo Mobile MFA tool can be found here. Microsoft has their own app as well. Authy allows you to do backups and migrate to a new phone and a lot of other housekeeping functions that the others don’t. There is still room for improvement with these apps as I personally would like to see the ability to create folders within the tool to manage similar types of access as well as biometric access to the app. However, the price is right.
Add MFA to all your apps
Next: Make sure that all-important websites you and your teams use have MFA enabled. Banking, Xero, LastPass, Jira, Bitbucket, Github, O365, AWS, Azure, etc. Then once you are done with your web apps, do the same thing on your phone apps: Banking, Rewards accounts and any other apps that are important to you and that you need for work. If it supports MFA, enable it and use your authenticator from #1 above. This function alone can save your ass more than anything else when you are being targeted.
You can check if your bank or other common websites support MFA here: https://twofactorauth.org
Banks are not doing enough!
Lemme vent about one of my pet peeves here: I don’t know why Australian banks have lagged so far behind on adding support for MFA apps to their web portals. NAB and CommBank both do NOT have MFA apps as an option on their web apps. CommBank will use a “NetCode” which is delivered in their app, but that’s only if you are authorizing a new payment or BillPay. What are you providing CommBank to protect my login to your NetBank and Web portal? CommBank, please up your game and offer support for MFA apps for customers that want to use it!
Cost: FREE
2. Password Manager

Install a password manager and then configure it to use multi-factor authentication (MFA) using the MFA you installed in #1 above. I personally use BitWarden, but I’ve heard good things about both 1password and Dashlane from friends of mine. Whichever tool you use, make sure that the master user and password are protected by MFA. MFA and a password manager are the two best things that a user can do to protect themselves. If you have employees I highly recommend you upgrade to the paid version of whatever tool you choose. You can then give each employee their own set of credentials and delegate required access.
- Bitwarden: https://bitwarden.com/
- 1password: https://1password.com/
- Dashlane: https://www.dashlane.com/
Cost: FREE
3. Endpoint Protection (AV/EPP/EDR)
Free tools used to be enough
Back in the day, I used free anti-virus tools like AVG and Malwarebytes and it was good enough. That’s not the case anymore. I can’t in good conscience suggest people do that in 2022. The threat landscape has changed too much, and for the worse. Instead, I recommend that you invest in a good “Endpoint Protection” (EDR) solution.
What is EDR?
EDR stands for “endpoint detection and response” and is the “next gen” version of anti-virus scanning technology and often leverages artificial intelligence to detect attacks. Most EDR solutions will provide a number of features for their platform including threat intelligence, and many of them now offer some form of ransomware protection for example. I am personally using CrowdStrike myself but we looked at several others including Cylance and SentinelOne. Most EDR solutions have a central management console that allows you to see and manage all computers you are managing with their platform. This is important as you want to make sure that all employees devices are up to date and have latest virus signatures, etc.

Whatever you do, make sure you get something with some ransomware protection built in. In fact, this probably needs to be another blog post about how to protect yourself from ransomware attacks. Stay tuned…
Cost: Starts at roughly $100 per employee per year.
4. Add Anti-Virus to Your Browser
Some EDR or anti-virus solutions require that you add a browser extension to your browser. A good example is BitDefender. Make sure that if your solution requires this extension, you have it installed. Otherwise, you might not be as protected as you think you are.
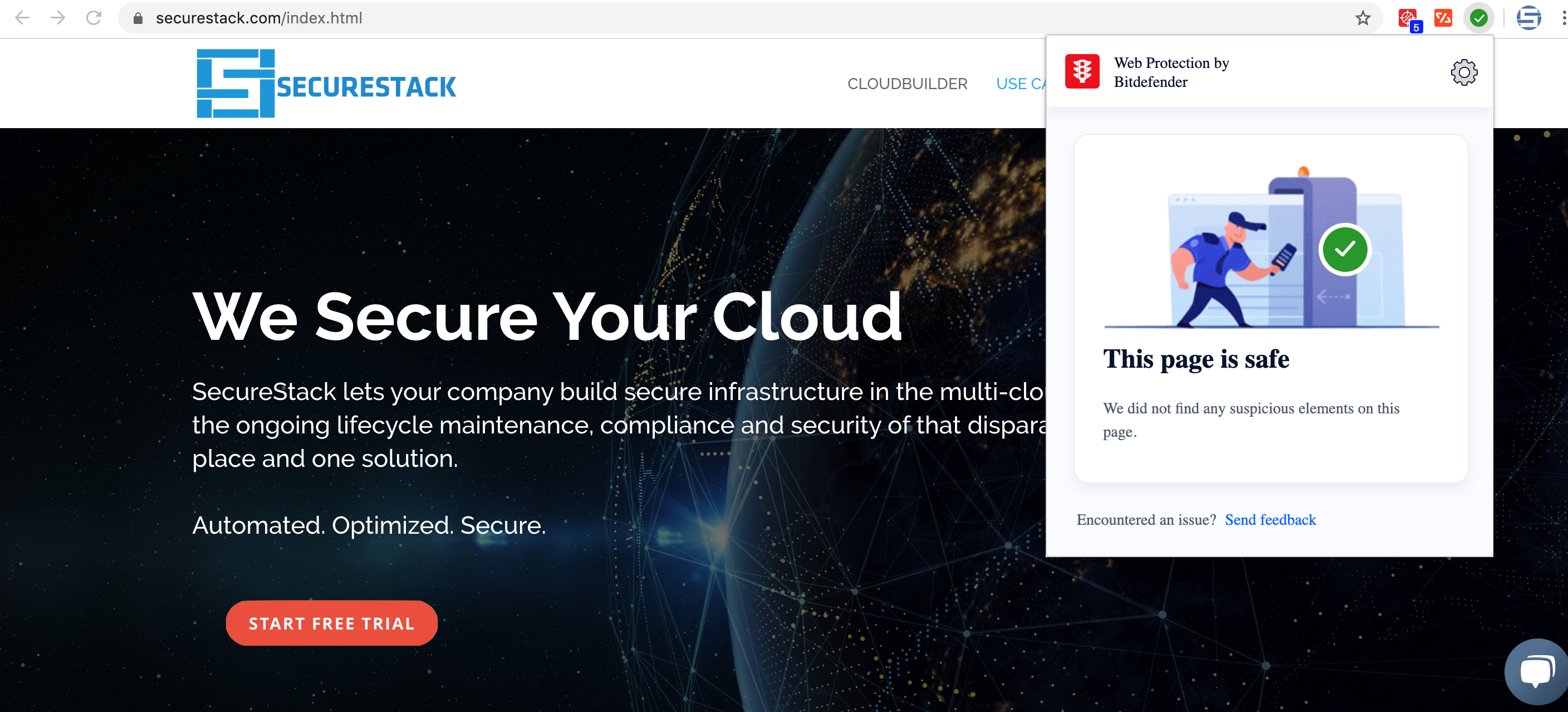
Cost: FREE (well, comes with paid subscription)
5. Sync Browser Data
Chrome:
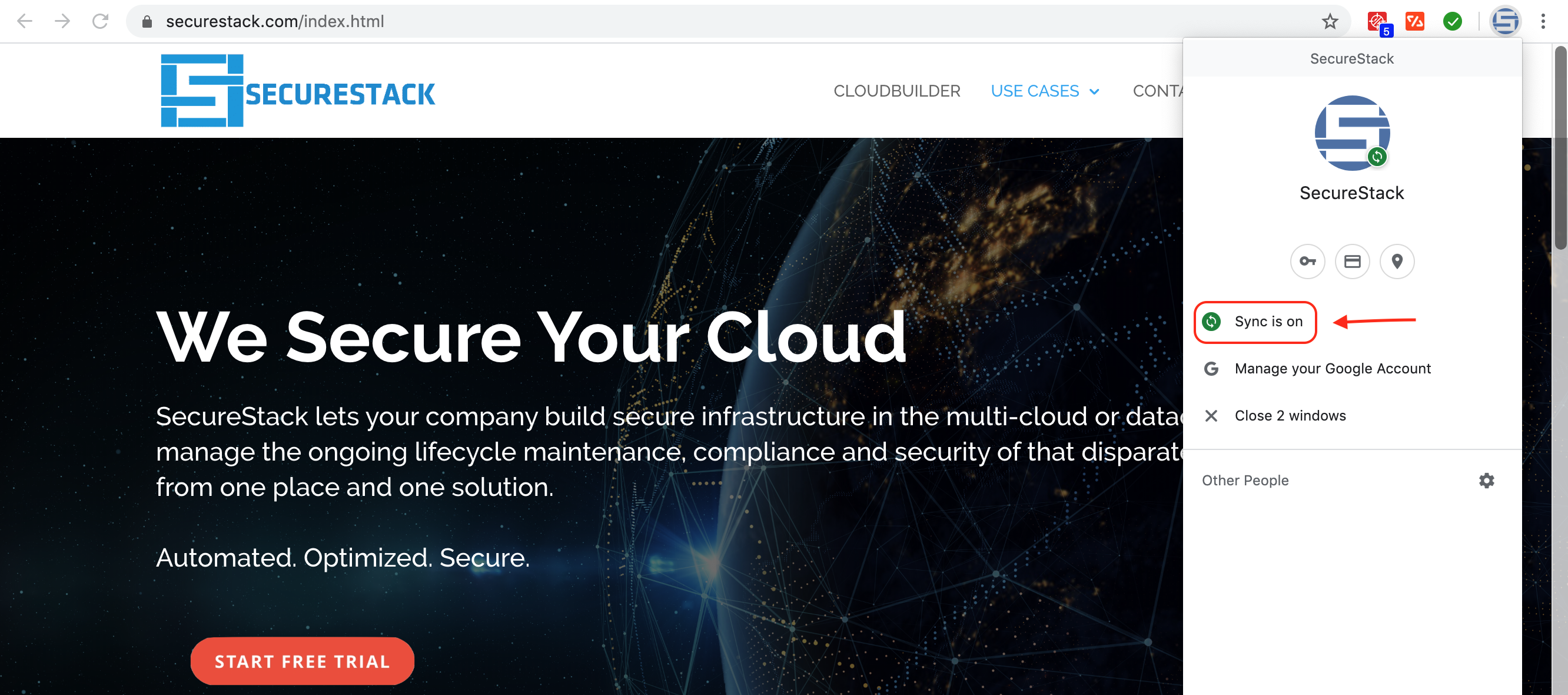
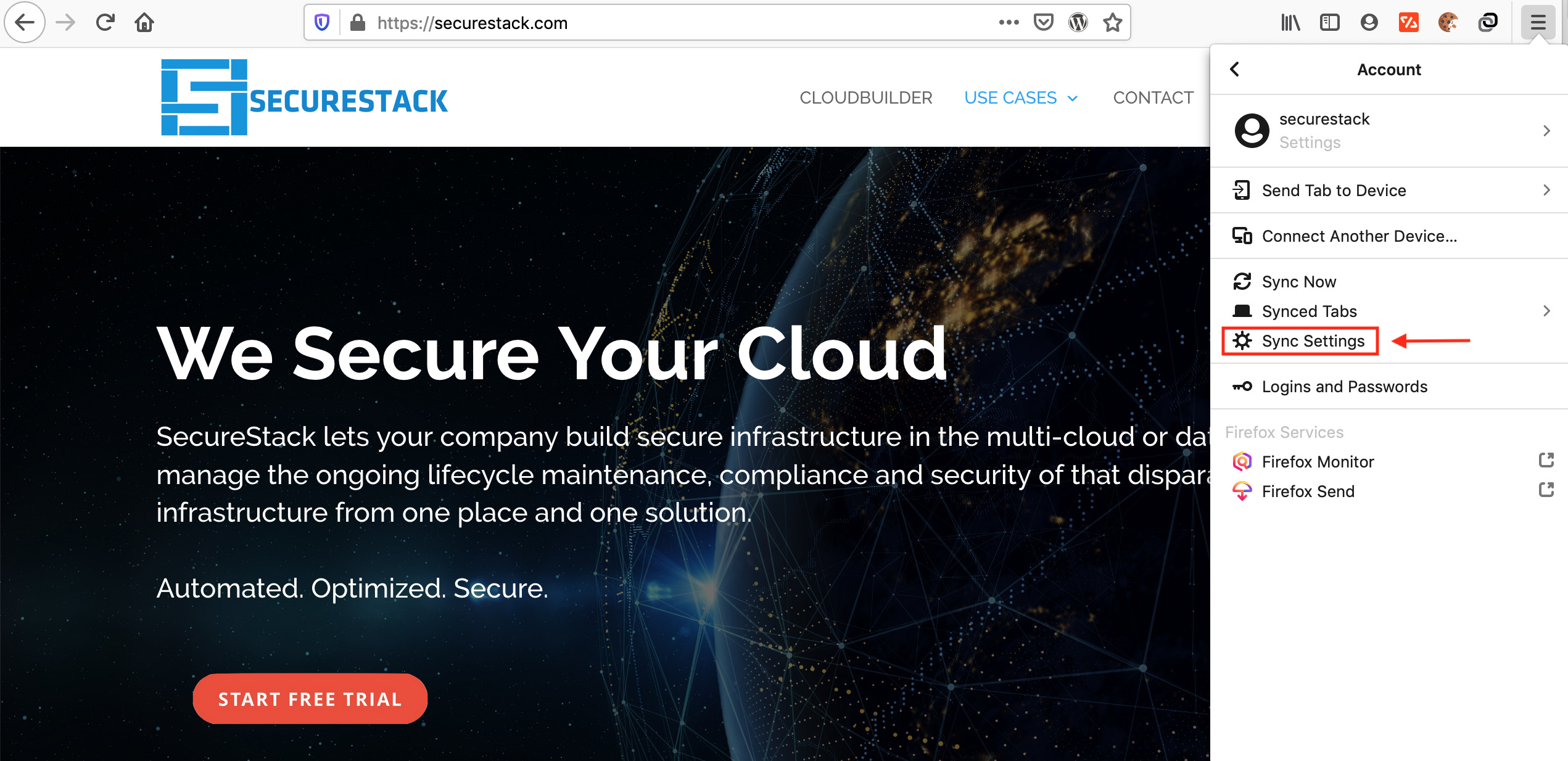
This is very helpful but is definitely a potential privacy concern. I’ve wrestled with this dilemma internally and have decided that the security and redundancy that having Google back up my stuff outweighs my personal privacy concerns. You can read about setting up Google sync here.
Cost: FREE
6. Backups
Backups are still the most important thing to have if you’ve been attacked
Setup backups for any important systems. This includes laptops and workstations, not just servers. Many companies think that because most of their business functions happen in SaaS applications that they don’t need to do backups anymore but my question then is, “how long would it take you to setup your laptop again to 100% working?” and “how long would it take to perform 100% of your business functions on a brand new laptop?”
Some helpful tools
CrashPlan, Carbonite, Backblaze and other online backups have cheap pricing for SMBs. I have personally used CrashPlan for years and have used it several times to restore family, friends and clients data after it was encrypted with ransomware.
If you are on a mac
One last minute addendum here: If you have a Mac I would recommend you use Time Machine. It’s simple and free but make sure you backup to a separate device at least once a week. Do not rely on a USB drive that’s always plugged in. If all your files are encrypted in a ransomware attack, that USB disk will be encrypted as well. So, pay for a couple 500G or 1TB drives and swap them once or twice a week. This article does a good job of explaining it.
Cost: FREE. Paid backup starts at $10 a month per computer
7. Update Software
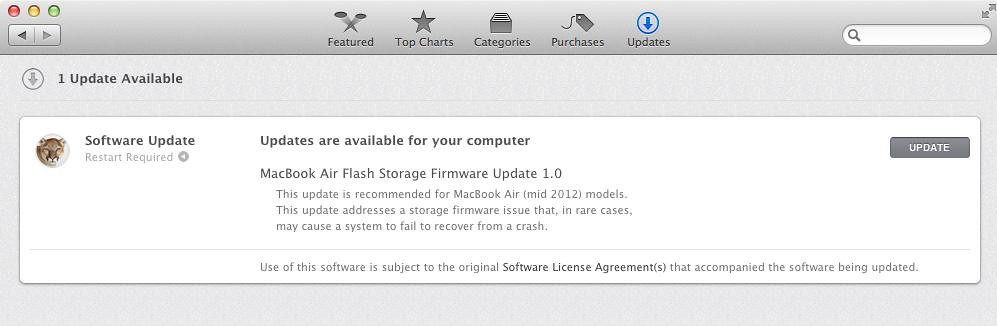
Software on your individual computer needs to be updated at least once a month, and preferably much more often. This applies to your desktop computers, mobile devices and any servers that you own or run. This is often a problem for that on-premise server that has been sitting in the corner for years serving up your files. When’s the last time it was patched?
If you aren’t patching, you are leaving yourself open to a host of potential threats and attacks. It’s similar to not getting vaccinated for diseases that you could easily protect yourself from. Set a day at least once a month, when you update and patch all your devices and services. Then block time for all your employees to actually do it.
Cost: FREE
8. Link Awareness
Be very careful about clicking on any links in an email, PDF, webpage or similar. See those links above? They look harmless, right? If you hover your cursor over them, and wait a second, the link will display what it’s going to. Train your staff to look and read the domain before they click. Clicking on unknown links is the origin of most ransomware and cyber attacks. Even worse, criminals have learned to register copycat domain names like hotrnall.com and office356-us.org which look legit at first glance, but send you to a copycat website. That fake site collects your real credentials and then sends you on the real website where you log in successfully not realizing what’s happened.
Consider applying other controls like endpoint protection or email filtering to limit the possibility of your employees clicking on the wrong link.
Cost: FREE
9. Security Awareness Training
Buy a Cynch membership. Cynch is the only cyber fitness platform designed for small business. They take the complicated technical jargon out and replace it with common sense plain language. Cynch helps small business define, quantify and address their cybersecurity related risk. Cynch is as little as $99 a month and it helps your whole team become smarter about cybersecurity while it protects your business.
These guys are friends of mine and are making a great difference here in Australia: https://cynch.com.au/
Cost: Starts at $99 a month
10. Phishing Awareness

If you don’t buy a Cynch membership, then at least buy some phishing training. There are cheap courses online in places like Udemy. I suggest you pay for something decent as phishing is one of the most successful ways that Australian businesses get scammed. The city of Brisbane alone has lost over $600k in multiple schemes this way. The phishing attacks have only grown in sophistication and are now coming from within Australia, so the person on the other end of the phone or email sounds like you and knows the same things that you do because they’ve studied your company and done their research. Potentially FREE, but you get what you pay for?
Cost: Varies, and some resources are FREE
11. Wifi Isolation
If your employees or guests can bring in their own computers, tablets, or connect their smart phones and connect to your company network, this is called “bring your own” or BYO.

Here’s what you can do to protect your wifi network
Have your IT team create a second wifi network for them called “Guest network”. Next, create complex but understandable passwords for both the guest and “Work” networks and be prepared to rotate them once a month at least. I know this is a pain in the ass but it protects you as all your neighbours will eventually get the password and if you don’t change it they will be living off your internet connection for YEARS. Finally, make sure none of your employees are violating this policy and make sure that all BYO devices are NOT on your work network. Your IT team can use some relatively simple methods to add only work computers to the work wifi (mac addresses bound to DHCP leases is a good example).
Understand that your internet connection is your responsibility. If someone uses it for illegal activity you could be liable.
Cost: FREE
12. SaaS Management
SMB companies use a lot of SaaS software. SaaS stands for “Software-as-a-Service” and describes software that you use through a browser that doesn’t need to be installed on your computer per se. How many SaaS applications does your company use? Common SaaS apps for SMBs are: Xero, MYOB, QuickBooks Online, Google Mail, Microsoft Office 365, Wix, and SquareSpace. Some common startup SaaS apps are: Mailchimp, Hubspot, Slack, Asana, Github, Bitbucket, Calendly, Basecamp, Airtable, Google Docs, Microsoft Office365, Sketch, Trello, Jira, Canva, and Pipedrive. There are obviously hundreds more that SMB customers use. SMB companies with less than 20 employees average at least 26 different apps in use. Startups often use an average of 100 or more SaaS applications.
Criminals are targeting the SaaS tools you use
Managing the logins, credentials, permissions, etc can be a real headache for people. Especially if you don’t have a dedicated IT person to handle it all. This is a real issue for many companies as they don’t keep track of the logins and credentials and then have to constantly reset the passwords for these SaaS tools. This ongoing behaviour makes it hard to catch a bad guy who does something similar. The email telling you about the password change (by the bad guy) gets lost in all the other legitimate password resets.
It’s important to define the SaaS assets and credentials that your company requires and use separate complex passwords for each SaaS app. Add all those logins to your password management tool from step 2 above and make sure that you protect that master account with a great password and a MFA app from step 1.
Once that’s all done make sure you add more than one person to the master account so if that person leaves or gets hit by a bus you have a backup admin that can retrieve those credentials.
Cost: FREE
13. Protect your intellectual property
Many businesses now have a new form of intellectual property that they need to protect. This is often in the form of custom software that they’ve had custom-built or modified for their use. If your company is SaaS-based, then this custom software is the heart and soul of your business and without it, you probably wouldn’t be able to function. But many “standard” types of businesses like real estate sales, or child care facilities, require software that has been modified to meet their requirements. In this case, unlike SaaS-based businesses they would probably still be able to function, but their business model would suffer without the software functioning.
This new class of intellectual property needs to be protected as it is often the target of very sophisticated attacks.

If you are going to host a web application, interact with customers online, sell online or use the web as a primary means to conduct business, you should take precautions to protect your digital intellectual property. SecureStack helps startups and scale-ups protect their software with our platform. It’s super easy to implement and you can be up and running in less than 20 minutes. Feel free to reach out by clicking on the button below.
Cost: Well worth it

Paul McCarty
Founder of SecureStack
DevSecOps evangelist, entrepreneur, father of 3 and snowboarder
Forbes Top 20 Cyber Startups to Watch in 2021!
Mentioned in KuppingerCole's Leadership Compass for Software Supply Chain Security!